Patches and data control: Keys to your organization’s security
November 2018, Chile. The bank Consorcio de Chile discovers that it has become the victim of an advanced cyberattack, a dangerous and undesirable situation for any company. If we add to this the fact that the attack involved the Trojan known as the nightmare of global banking, and the fact that this particular nightmare managed to steal 2 million dollars from the bank’s funds, the outlook is extremely disheartening.
Analysis of EMOTET
The Trojan in question is called Emotet, and Chile is just the latest country on its list of victims—a list that already includes countries such as Germany, Switzerland and the United States. But what is Emotet, how does it spread, and what damage can it do?
Emotet is a polymorphic banking Trojan. Its main goal is to steal data such as user credentials, or to spy on network traffic. It is also frequently used to download other malware, including other banking Trojans.
The most common propagation method for this Trojan is email, whether via infected attachments or embedded URLs. One particularly dangerous feature of Emotet is that it takes over its victims’ email accounts. This helps to trick other users into downloading the Trojan onto their systems.
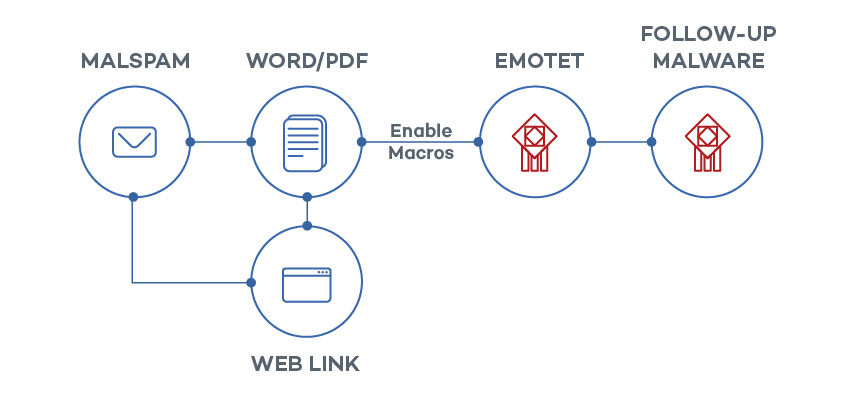
Once Emotet has infected a computer on a network, it uses the vulnerability EternalBlue to get to other endpoints on unpatched systems.
The most serious damage
The most serious consequences that an organization can experience as a result of an EMOTET attack include:
-Theft of personally identifiable information (PII).
-Leaking of financial and confidential information, which can be used for blackmail.
–Theft of login credentials, making other accounts vulnerable
–Long remediation periods for network administrators.
–Loss of productivity of employees whose endpoints have to be isolated from the network
It is clear that this malware would be a serious danger for any company it managed to infiltrate. This is why at Panda Security, we recommend having the best preventative protection against any kind of malware, both known and unknown. This is what Panda Adaptive Defense does, since it stops all malware from running, as well as keeping endpoints updated.
In our whitepaper, Patches and data control: Keys to your organization’s security, you can find more information about the risks that this Trojan can entail, how it can get into your company, and how Panda can help you to avoid the most drastic damages.
Fuente: https://www.pandasecurity.com/
Fecha de consulta: 11 enero 2019



